What is Net iD Access Server?
Net iD Access
Net iD Access is a user authentication service, which also provides digital signatures, using smart cards or soft tokens. Net iD Access gives a complete solution for both desktop and mobile security using client-side applications and the server component Net iD Access Server.
Net iD Access separates the information channel from the security channel. This gives a number of possible setups, which are selected through the configuration of each service. It is also possible to do authentication using either soft tokens or smart cards.
The solution ties together the client’s service applications and server-side without the need for advanced PKI development. The client can choose to handle the validation and revocation checking in Net iD Access Server, or on the server-side in the services.
Net iD Access applications
Net iD Access is available as an application on all major operating systems, both mobile and desktop. To enable switching between Net iD Access and browser/service application, an operating system-specific call must be implemented in the websites/service application. Net iD Access uses PC/SC or CT-API (card reader and smart card) to get smart card support.
Net iD Access applications are available on the following platforms:
-
Microsoft Windows
-
macOS
-
Linux
-
Android
-
iOS.
Net iD Access Server
Net iD Access Server is a server component that handles communication between Net iD Access applications, service provider servers, and the underlying PKI infrastructure’s revocation information (via Windows integrated features for OCSP and CRL). Which services Net iD Access will be used for and which certificate issuers are approved for access to the service are configured in Net iD Access Server.
Net iD Access Server is installed as a web service under Microsoft Internet Information Server (IIS). Configuration is handled via an XML file.
All information exchange between Net iD Access applications and Net iD Access Server takes place via TLS/SSL for integrity protection. Two-way TLS/SSL is required between the service’s servers and Net iD Access Server.
Net iD Validator 1.1
If a certificate is revoked by the issuing certification authority (CA), it is listed by the issuing CA in the CA database (OCSP) and/or a certificate revocation list (CRL). If the performance of the Windows built-in certificate validation is unsatisfactory, you can use the add-in program Net iD Validator. Net iD Validator bypasses Windows built-in process and makes its own check if the certificate is revoked.
-
OCSP – Is used if the client certificate contains information to use an OCSP responder.
-
CRL – If the OCSP information is missing, Net iD Validator checks its local CRL file. Net iD Validator will automatically keep this CRL file with revoked certificates up to date.
Net iD Validator can also make a check that a signature is valid and has not been compromised.
Use cases
One use case is to use the same device for both login and authentication, and another one is to put these functions on different devices. Devices can be anything from mobile devices to desktop or tablet computers. Both soft tokens and smart cards can be used for authentication.
Furthermore, access to critical services can be limited so that they are only accessible from the device with a smart card.
Use case example
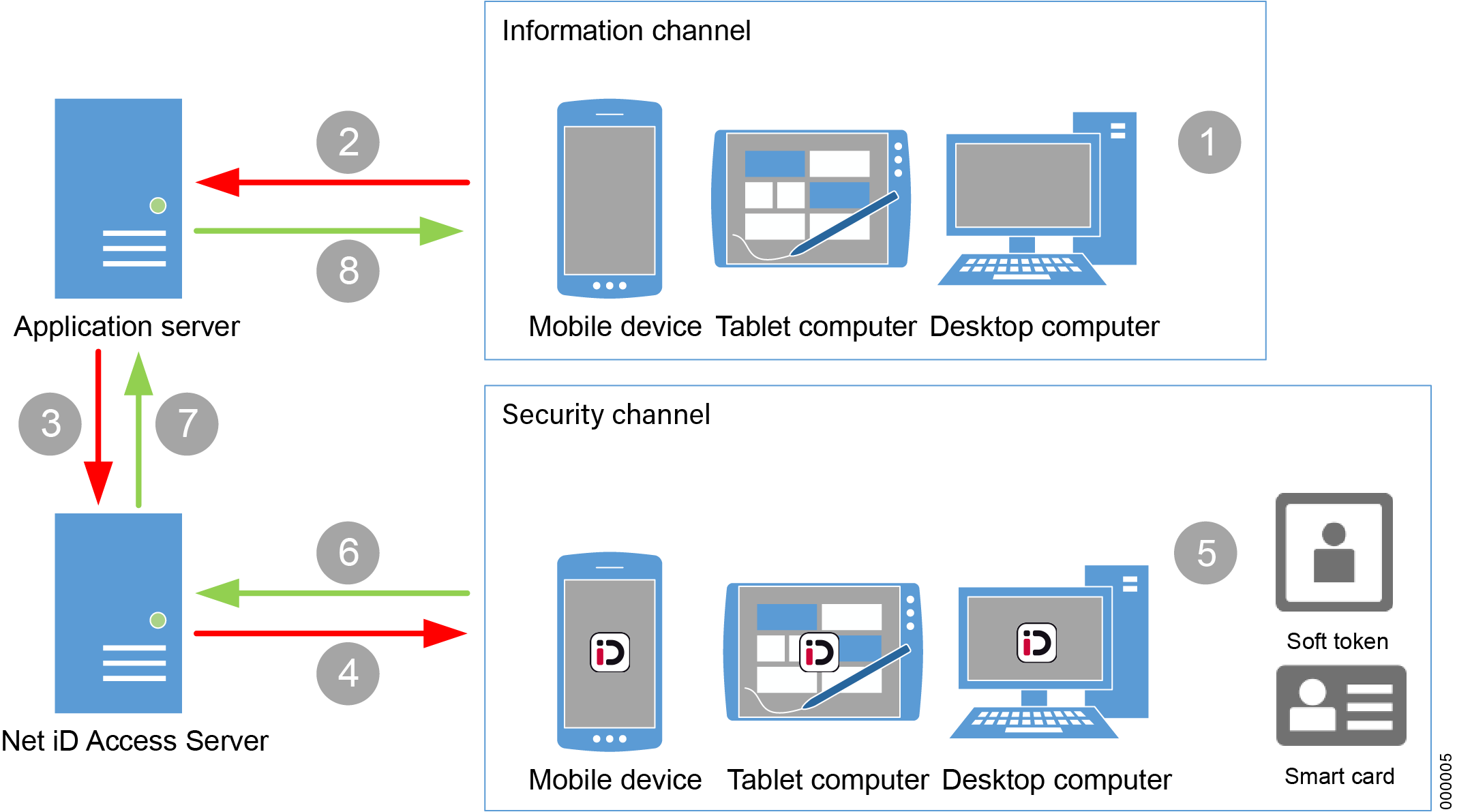
| Step | Description |
|---|---|
1 |
In the service application, the user types the user ID to log in to the service. |
2 |
The service application passes on the user ID to the service’s application server. |
3 |
The application server sends a login request for the user to Net iD Access Server via a simple web service call. |
4–6 |
The user is at the same time switched over to the Net iD Access application, and the actual smart card-login is done through Net iD Access Server. |
6–7 |
Net iD Access Server verifies the user and notifies the application server. |
8 |
The user is automatically switched back to the service application and gains access to the requested service. |